The oil and gas industry is an important segment of the global economy. There are millions of people around the world working in the industry. They are responsible for powering homes, businesses, transportation systems, as well as supporting trade, technological upgrades, infrastructure development, etc. Like most industries today, oil and gas companies increasingly rely on digital technology – making implementing an information security strategy more important than ever.
Key differences between segments in the oil and gas industry

Oil and gas is one of the world’s largest industries. The industry is divided into three main segments: upstream, midstream and downstream. Each industry segment is interconnected and plays a vital role in ensuring efficient production, transportation and distribution of petroleum products. However, these segments have some key differences. Therefore, having an effective information security strategy depends on the segment of each company. Here are the main differences:
- Upstream:
The upstream segment focuses on finding, exploring, and exploiting crude oil and natural gas. Midstream and downstream companies will transport and refine into fuels, chemicals and other finished products. Upstream has many different methods of extracting materials, including through oil wells and rigs, offshore drilling, oil sands mining, and fracking.
Upstream activities often take place in remote and dangerous environments. At the same time, their assets are often distributed over large geographical areas. This characteristic can cause difficulties for upstream companies. Not only in monitoring and securing their entire operations and assets, but also performing software updates, applying patches, and implementing other necessary security controls. As a result, upstream oil and gas systems tend to be more exposed and vulnerable to cyberattacks.
- Middle source:
The midstream segment includes the transportation and storage of crude oil and gas materials. Midstream companies typically use pipelines, tanks, tankers and/or other specialized facilities to store and transport crude oil and natural gas from upstream production sites to facilities. downstream oil processing and refining, or distribution to customer hubs. Like upstream organizations, midstream architectures tend to be widespread and geographically dispersed, causing challenges in cybersecurity monitoring and often unsecured remote access.
These organizations’ ongoing dependence on pipelines to transport oil and gas, as well as their reliance on third-party contractors to provide equipment and services, also strongly contribute to the challenges. their remote access. By targeting pipelines or exploiting inherent vulnerabilities of third-party vendors, hackers can gain unauthorized access, disrupt operations, and even cause physical damage.
An incident like this once happened to the Colonial Pipeline (USA), affecting the transportation of oil and gas, and causing fuel prices for consumers to increase, among many other consequences. We will discuss this unprecedented attack on US critical infrastructure further later in this article.
- Downstream:
The downstream segment focuses on processing raw materials obtained upstream. This involves converting crude oil into usable products such as gasoline, diesel and jet fuel. It also involves the distribution of these products through a network of pipelines, tankers and retail outlets (i.e. gas stations) to consumers. Downstream network architectures tend to be more closely related to those in traditional “factory” environments, found in other industries, such as manufacturing and power.
The physical processes that underpin downstream environments often rely on legacy systems and devices — most of which were not designed with security in mind. Because these systems and devices are often too old or fragile to support software updates, they tend to contain both known vulnerabilities and zero-day vulnerabilities that can be easily exploited by attackers. . Additionally, as IT and OT converge, industrial control systems (ICS) located in these environments are increasingly connected to the internet. This connectivity has expanded the attack surface for down stream organizations, making them more vulnerable to cyber risks.
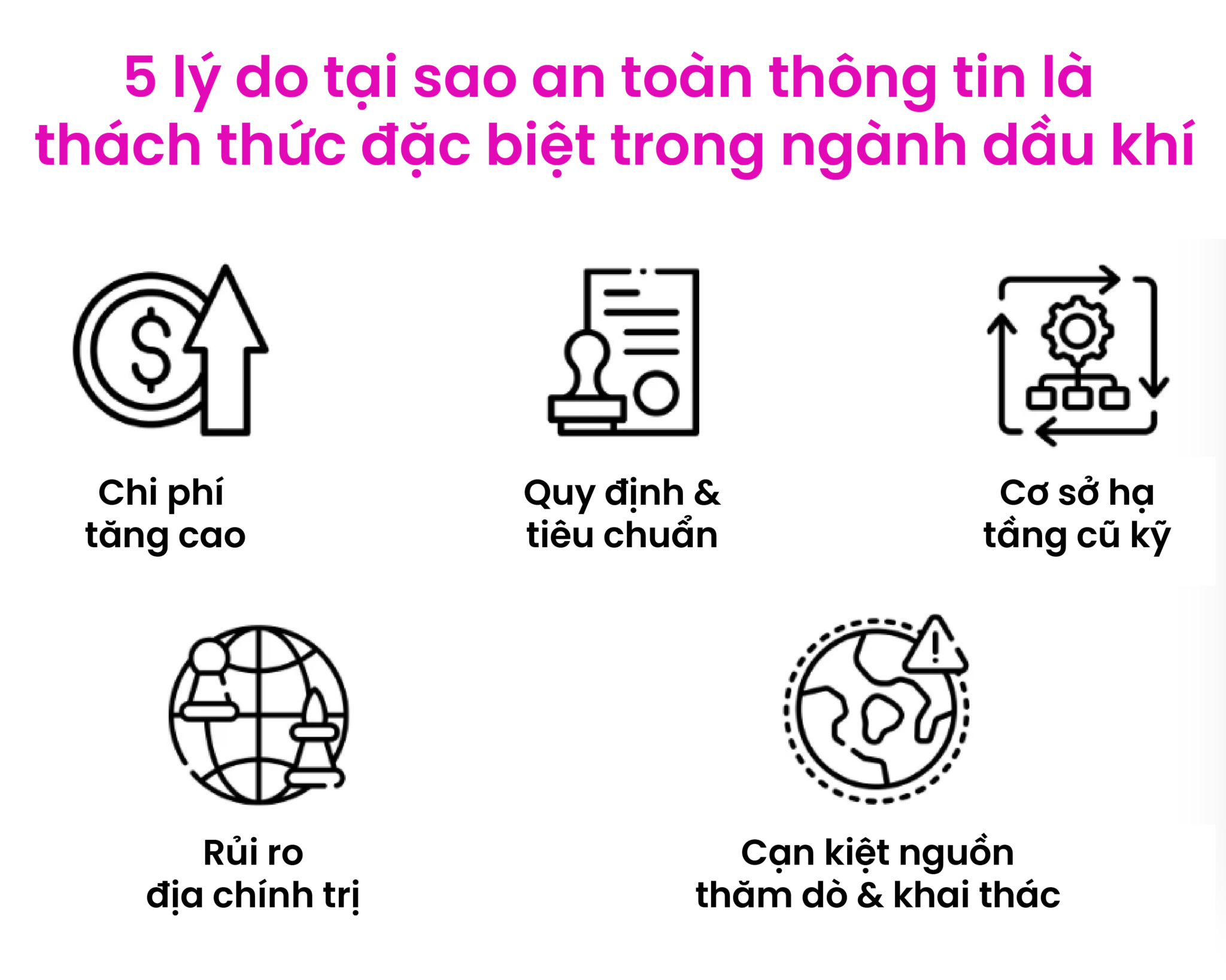
5 reasons why information security is a special challenge in the oil and gas industry
The oil and gas industry faces a number of challenges that require innovative solutions and strategic partnerships to help them adapt and respond to these challenges.
The first challenge that companies in this industry face is the highly volatile oil and gas prices. Barrel prices are subject to a range of geopolitical, economic and environmental factors. This makes it difficult for companies trying to plan and implement long-term projects and investments. This problem especially affects upstream development because it is directly related to oil prices. More complex upstream methods such as oil sands refining and offshore drilling will stop working if oil prices fall too sharply.
This challenge also puts pressure on upstream oil and gas companies to keep costs as low as possible. Many times, there is pressure on them to reduce spending on information security initiatives. With limited resources to invest in robust security technologies, companies are left with unprotected systems and devices. Ultimately, failure to prioritize information security can lead to major financial losses, reputation damage, and regulatory fines.
The second major challenge facing oil and gas companies is the increase in regulations and standards that are shaping the industry. Largely due to recent cyber attacks in the industry, new regulations regarding cyber security requirements for pipeline owners and operators have been approved by the Transportation Security Administration (TSA, USA) show.
While these regulations impact midstream companies most directly, many larger organizations are also at risk due to their size. With continued threats to critical infrastructure, regulations will continue to evolve to minimize risks. This makes oil and gas companies focus on implementing appropriate information security strategies. Additionally, this can be extremely costly for small and medium-sized oil and gas companies. Without a dedicated team or partnerships with information security vendors, companies will not only have difficulty meeting requirements but will also be unable to improve their cyber security posture.
The third major challenge concerns aging infrastructure. Much of the oil and gas industry’s infrastructure, especially in the upstream and down stream sectors, is old and in need of repair or replacement. The challenge is that the cost of upgrading equipment in pipelines, refineries and production facilities is often higher than the expected commercial output over the life of the plant. This makes it difficult for projects to be accountable, causing old equipment to remain in place.
These legacy systems and outdated technology also pose significant oil and gas information security risks, as they were not designed with security in mind. Many times, they don’t have the latest software updates or security patches, making them more vulnerable to attacks.
Another notable challenge stems from geopolitical risks. The oil and gas industry faces a number of challenges when it comes to geopolitical risks including trade tensions, controls and instability in producing countries. These risks could affect oil and gas reserves and prices, making it more difficult for companies to operate in certain regions. This can be seen today with the distribution of energy trade between Europe and Russia. This has pushed the price of the global gas market to increase sharply – six to ten times the price of the US Henry Hub, according to Deloitte’s 2023 oil and gas industry outlook.
Such political instability has the potential to create an unstable cybersecurity environment, making it difficult for companies to protect sensitive information and operations. Geopolitical risk can also occur in the form of cyber terrorism, which is often carried out with the intent of disrupting operations or causing physical damage, and can be difficult to prevent or detect. Overall, these risks have a significant impact on cyber security as attackers seek to access sensitive information, disrupt operations, or steal intellectual property.
According to many upstream companies, easily collected sources of oil and gas have been exploited to the point that many sources are considered empty. Currently, more expensive and complex methods such as oil sands, offshore and fracking are being used.
These methods increase the costs of finding new sources, making upstream companies even more exposed to oil prices. They have also improved upstream companies’ reliability of OT systems, ICS systems, and surveillance and data acquisition (SCADA) systems. These systems are important for exploration and production operations because they increase efficiency and safety. However, their connectivity has further expanded their attack surface — making them more vulnerable to cyberattacks.
Notable cyber incidents in the oil and gas industry
There have been many recent cyber security incidents that have built on and/or increased the above challenges for oil and gas companies, as well as making it important to implement an information security strategy.
One of the major incidents that has plagued the oil and gas industry was the ransomware attack on the East Coast’s largest gasoline, diesel and natural gas distributor, Colonial Pipeline. The attack on Colonial’s IT network caused the company to shut down pipelines, causing gas prices to rise and in some states, and consumers scrambling to find gas at the pumps. In particular, the Colonial Pipeline incident became a catalyst for increased cybersecurity regulation in the industry. At the same time, it’s a wake-up call for executives when establishing a strong cybersecurity strategy across their organization.

As we increasingly see, ransomware has become a scourge on businesses worldwide and attacks are predicted to increase in number and complexity.
Another recent incident affecting oil and gas cyber security was an attack targeting oil loading facilities at the Amsterdam-Rotterdam-Antwerp (ARA) refining hub. This attack caused significant controversy regarding the loading and unloading of refined product cargo because many of these processes are automated. The impact is evident on the flow of oil products such as heating oil, diesel, jet fuel and gasoline.

This cyber attack would not only have devastating consequences for ARA’s business, but could also have wide spread economic and social impacts across Europe. The ransomware attacks on the ARA refinery were very similar to the US Colonial Pipeline incident a year earlier, and further demonstrated that cyber criminals are exploiting the shortcomings of the oil industry’s defenses “What is the gas like?”
Both of these attacks impacted critical infrastructure across the economy and society. We are increasingly seeing a growing need to secure legacy systems, (which are not fully protected due to digital transformation), and their increasing ability to connect to the Internet. These attacks also spurred government action on the importance of cyber security, which can be seen clearly in the regulations and standards listed below.
Information security regulations and standards important to the oil and gas industry
Following the ransomware attack on Colonial Pipeline, we have seen unprecedented action from the US government regarding mandatory incident reporting procedures and enhanced cybersecurity measures from owners. and petroleum pipeline operators. Here are some important cybersecurity standards and regulations that have been introduced:
- TSA Security Directive
As discussed earlier in this article, TSA issued a pipeline security directive with the goal of reducing the risk that cyber security threats pose to critical pipeline systems and facilities. The directive requires TSA-designated liquefied natural gas and pipeline owners and operators to implement three cyber security measures to prevent disruption and degradation of their infrastructure.
While this directive came as a shock to many oil and gas companies, it is a step in the right direction for companies to make better decisions regarding cyber policy, awareness, training and skills development for a comprehensive cyber security program.
- International Electrotechnical Commission (IEC) standards
IEC has also developed a series of international standards for the protection of industrial automation and control systems (IACS). The oil and gas industry relies heavily on IACS to manage and monitor critical operations, making the IEC 62443 standard an important tool for companies in this industry to follow. They provide a comprehensive framework to address the cyber security needs of IACS, which is particularly vulnerable to threats due to its interconnectedness and reliance on legacy technology.
Implementing IEC 62443 standards can also help oil and gas companies comply with regulatory requirements, including those issued by the U.S. Department of Homeland Security (DHS) and the Petroleum Producers Association. international gas (IOGP) set out. These standards can be seen as essential tools for companies to ensure the security and resilience of their critical infrastructure.
- ISO/IEC 27001
Another globally recognized standard for information security management systems (ISMS) is ISO/IEC 27001. This standard significantly impacts oil and gas cybersecurity because these companies rely heavily on into IT and handling large volumes of sensitive data. With ISO/IEC 27001, oil and gas companies can establish a comprehensive framework to manage and protect the confidentiality, integrity and availability of sensitive information – including exploration data and production, financial data and personal data of both employees and customers.
Like IEC 62443, ISO/IEC 27001 can help organizations comply with legal requirements, including those imposed by DHS and the European Union’s General Data Protection Regulation (GDPR). Overall, by implementing this standard, oil and gas companies can protect sensitive data against cyber threats and maintain a safe and secure operating environment.
- NIST CSF
Although there are a number of other regulations and standards that the oil and gas industry must comply with today, the final cybersecurity framework we will discuss in this article is that of the National Institute of Standards and Technology (NIST). CSF). This framework provides a set of guidelines, as well as best practices, for organizations to manage and mitigate cyber security risks.
NIST CSF includes five core functions: Identify, Protect, Detect, Respond, and Recover. These capabilities enable organizations to prioritize threats, focusing resources on areas of highest risk. Like IEC 62443 and ISO/IEC 27001, NIST CSF can help oil and gas companies comply with regulatory requirements, including those imposed by DHS and NERC. By applying this framework, oil and gas companies can enhance their operational and network resilience. At the same time, it helps reduce the likelihood of future network incidents.
These regulations and standards provide a solid framework for oil and gas cybersecurity across all sectors, to help manage risk, protect sensitive data, and comply with industry regulations. By following the directives, standards and frameworks outlined above, the oil and gas industry can ensure they have the appropriate security measures in place to meet these requirements and to protect critical infrastructure.
Vina Aspire is a consulting company, providing IT solutions and services, network security, information security & safety in Vietnam. Vina Aspire’s team includes skilled, qualified, experienced and reputable experts and collaborators, along with major domestic and foreign investors and partners to join hands in building.
Businesses and organizations wishing to contact Vina Aspire Company with the following information:
Email: info@vina-aspire.com | Website: www.vina-aspire.com
Tel: +84 944 004 666 | Fax: +84 28 3535 0668
![]()
Vina Aspire – Vững bảo mật, trọn niềm tin