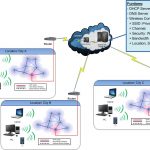
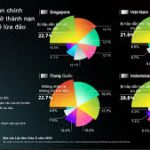
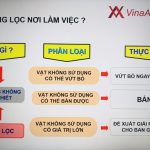
Nowadays, the types of cyber attacks are changing day by day, and with the change of the Internet of Things, industrial networks and other situations, technology is also developing rapidly and the level of competition between attack and defense is getting higher and higher.
From the perspective of those in the industry, the potential risk of cyber attacks is huge. In businesses with Internet access, although they have heard about security, it is all limited in technical vocabulary that is difficult to pronounce. Party B considers Party A a “muggle” and Party A considers Party B a “magic stick”.
Based on this, some security companies started looking to work hard on product architecture and launch products for different scenarios to meet more and more challenges. To sum it up in one sentence: The cyber security industry needs to be upgraded urgently, otherwise, for the large number of companies connected to the Internet, the future may not only face big storms.
Compared with other factors of production, data has the following characteristics:
Unlimited copying and transmission: Unlike production factors such as materials and labor, data can be copied and transmitted without limit. This means that data is not worn out or lost during use and can be used in multiple places at the same time, increasing the value of the data.
Non-exclusivity: use of the data does not exclude use by other people or companies, and use of the data by one person does not prevent others from using the same data. It also means that data can be shared between different applications and purposes, increasing the flexibility and usefulness of the data.
High variability: Unlike other factors of production, data is by its nature subject to continuous change. Data can be processed, combined, analyzed and interpreted to create new data and information. This also means that the value of the data can constantly change depending on how the data is processed and analyzed.
Get technical support: Collecting, storing and processing data requires technical support. This means businesses need to invest a lot of technology and resources to support the collection and use of data, while also needing to protect the safety and security of data.
That means, precisely because of the characteristics of data, different policies and management methods need to be developed to protect the security of data. Several companies interviewed mentioned to Digital Planet: “It is important to protect high-value data assets from destruction.”
To expand, if highly valuable data assets are destroyed or accessed, used, or disclosed, the modifications could have a serious adverse impact on national security interests, foreign relations , economics, public confidence, civil liberties or public health and safety.
For enterprises, highly valuable data assets have been deeply involved in the enterprise’s decision-making process, and have even become the core innovation and competitiveness of enterprises.
Data is important, but according to the results of many studies conducted by Digital Planet, companies still do not fully understand it. In other words, businesses today generally lack the ability to manage data, a new factor of production.
Objectively speaking, for some well-known reasons, some cybersecurity challenges do not appear on paper. However, in general, as mentioned above, today’s cyber security industry has reached a new stage of development.
This has accelerated the process of transforming management thinking.
In the past, cyber security companies tended to develop a “perfect attack and defense strategy” to deal with challenges. With the passage of time, this type of thinking is still criticized as “too idealistic”. While attack and defense strategies are an important part of cybersecurity, it can help cybersecurity companies and customers improve their ability to protect, prevent, and respond to attacks. cyber attack. However, because cyber attacks are difficult to predict and uncontrollable, it is difficult to build a perfect attack and defense strategy that can only be continuously optimized and updated to adapt to changes. changes and developments in network security.
Therefore, to date, many companies have proposed the concept of “cyber resilience”.
The term resilience refers to the ability to quickly restore normal business operations and functions in the face of cyber threats and attacks.
Improving flexibility has at least the following major benefits:
First, cyber resilience can help cyber security companies and customers establish a more realistic and agile security mindset that focuses not only on defense and risk avoidance, but also focus more on resilience and adaptation to risks, thereby improving the sustainability and stability of cyber security.
Second, cyber resilience can help cyber security companies and customers establish a more comprehensive and systematic security management system that does not rely solely on technology and products but focuses on more into the organization and strategy, thereby improving the coordination and effectiveness of cyber security.
Third, cyber resilience can help cyber security companies and customers establish a more open and collaborative security ecosystem, instead of isolating themselves and relying on external resources for innovation. Improve mutual trust and innovation in cybersecurity.
It is important to note that cyber resilience is not just a technical issue but also a management and strategic issue. Cyber resilience needs to be established on the basis of cyber security, through effective risk assessment, contingency planning, emergency response, recovery measures, etc., to enhance capabilities resilience and adaptability of network systems and organizations.
The security industry needs to be taken seriously
Currently, implementing cyber resilience requires the following types of technical support:
Some people in the industry have frankly admitted that the above technologies will improve the level of cyber security to a certain extent. The ubiquity of cyber resilience brings the following benefits:
Now, globally, the cyber security industry is catching wind: In the fourth quarter of 2022, the global cyber security technology market grew 14.5% to $19.6 billion. Of which, spending on purchasing cyber security technology through channels accounts for 91.8% of the total market share, reaching 18 billion USD.
For the whole of 2022, the global cyber security technology market will grow by 15.8%, reaching 71.1 billion USD. Of which, spending on purchasing cyber security technology through channels accounts for 91% of the total market share, reaching 64.6 billion USD.
The transformation of cyber security may have begun quietly, and the industry may actually be “changing.”
Vina Aspire is a consulting company, providing IT solutions and services, network security, information security & safety in Vietnam. Vina Aspire’s team includes skilled, qualified, experienced and reputable experts and collaborators, along with major domestic and foreign investors and partners to join hands in building.
Businesses and organizations wishing to contact Vina Aspire Company with the following information:
Email: info@vina-aspire.com | Website: www.vina-aspire.com
Tel: +84 944 004 666 | Fax: +84 28 3535 0668
![]()
Vina Aspire – Vững bảo mật, trọn niềm tin