Trend Micro’s analyzes are gradually clarifying Hacker behavior, what time of the week they usually attack and what days are most likely, as well as how they share attack data.
Real threats can come from any day of the week. However, there are still attacks at certain times, many businesses will often want to know this, because they are often lax, especially on weekends and Hackers will rely on that to attack. These may not be the types of questions that cybersecurity professionals often think about, but their implications can actually have important implications for how to better align resources and strategies to develop detect and protect against attacks.
In their Q1 2019 report, analysts at FortiGuard labs spent some time researching this behavior of Hackers and this is what they found.
Why do these behaviors occur and what causes this to happen?
Why do we distinguish between weekdays and weekends? Our analysts have hypothesized about this and they suspect that Hackers will attack almost periodically. Because when attacking a large company’s server, they will need a large number of bots as well as the help of many people. In theory, if a Hacker acts alone, it will be difficult to succeed. That’s why they often attack in groups.
What day of the week do hackers usually attack?
Contrary to what people often think, Hackers will not focus their attacks on weekends. Our research shows that attacks are three times more common on weekdays than on weekends. Trend Micro believes that this happens because Hackers want to rely on daily internet activity to find loopholes to security flaws, thereby making attacks easier and they can also stay ahead of them. Let’s take a step so that we think that the weekend is a good time.
We realized this when testing data exfiltration filters at cybersecurity partners around the world. The unusual amount of traffic on weekdays made us suspicious and analyzed, unintentionally opening a new picture of hacker attacks on businesses.
Most of the time, attacks will increase at the beginning of the year, then gradually decrease in the middle of the year and at the present time, there are signs of increasing again, possibly at the end of the year when there are online shopping programs and This is definitely an opportunity for them when many people use online payments
Hacker’s attack method is recorded
With the collected statistics, our researchers obtained a graph of the attacks as well as the attack methods recorded. In this case, we collected metrics from our partner businesses’ traffic filters.
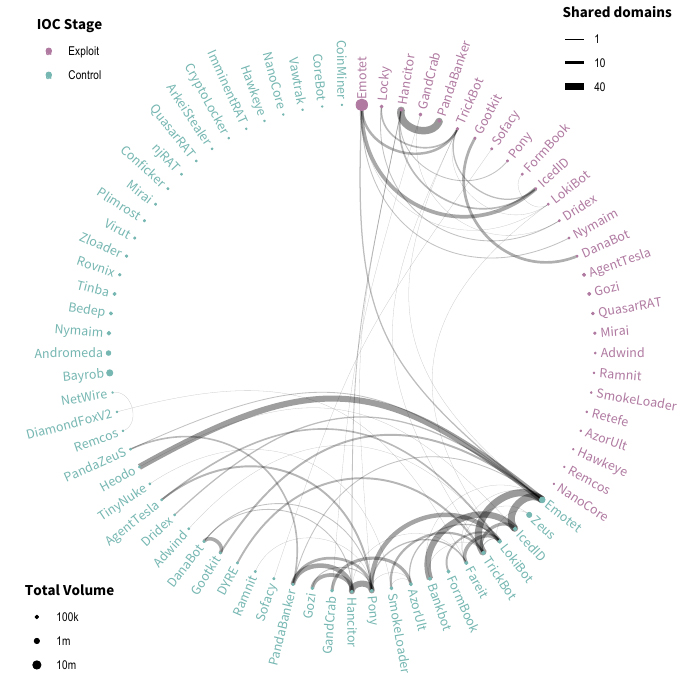
Statistical map of Viruses used by Hackers to attack.
An additional aspect of web filtering data that researchers found noteworthy was the extent to which different threats shared infrastructure (specifically URLs). The figure above shows this overlapping infrastructure in a circular network diagram. Each node represents malware or botnet communication generated by threats during the control phases of the Kill Chain. The thickness of the lines represents the number of domains shared between threats at each stage. The size of each node corresponds to the total mass detected in Q1. This data provided some interesting observations that our experts marveled at.
Trend Micro will have a solution that will be secure regardless of time?
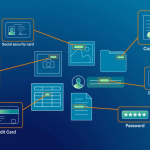
For individual users, we encourage you to use the simplest security solution, which is genuine Trend Micro Maximum Security anti-virus software. Because for individual users, just that is more than enough. This solution will have warning features to help you feel secure when accessing any website as well as a defense layer when there is unusual access to your computer.

Worry-Free solution is considered a way for businesses to prevent hacker attacks.
For businesses, Worry Free Solution is being used by many businesses globally because of its centralized management capabilities, ease of use, and always being ready to protect businesses whether it’s during the week or not. weekend. Combining AI technology (artificial intelligence), our solution helps you filter fake emails with a smart processor, recognizing the writing style of each partner’s email. Helps you escape the traps that Hackers set.
Be secure before malware invades!
Vina Aspire is a consulting company, providing IT solutions and services, network security, information security & safety in Vietnam. Vina Aspire’s team includes skilled, qualified, experienced and reputable experts and collaborators, along with major domestic and foreign investors and partners to join hands in building.
Businesses and organizations wishing to contact Vina Aspire Company with the following information:
Email: info@vina-aspire.com | Website: www.vina-aspire.com
Tel: +84 944 004 666 | Fax: +84 28 3535 0668
![]()
Vina Aspire – Vững bảo mật, trọn niềm tin